by E.I.T. Author | Feb 1, 2017 | Blog, Computers, Security, viruses
Are you a person who sometimes gets viruses or malware on your computer, and you swear you didn’t install it, but you did, and you can’t figure out how or when it got slipped in there? Well I’m going to show you a common one that people miss.
The problem now is, that hackers KNOW that most people select the DEFAULT, QUICK installation when they install things. So they hide them there. The solution? DON’T! Don’t select the default option when installing programs, EVER. Always choose the “ADVANCED” or “CUSTOM” installation when installing things. Always! I guarantee that 90-95% of the time, there is a toolbar, or some additional program installation needing your approval, set up in the default installation, and if you choose default, you “WILL” authorize it’s installation. I’m going to show you a picture, and as I run across other examples, I will come back and add more pictures to this post. But for now, I have two from today.

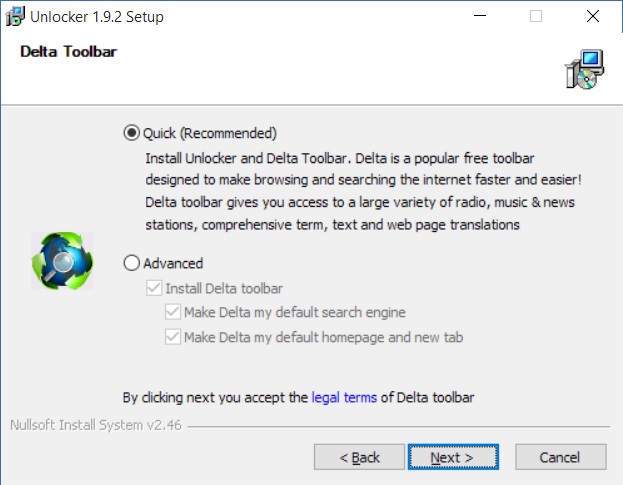
Hidden Toolbar in default program installation
Notice, that “if” I were to select the ADVANCED option, ONLY THEN can I UNCHECK the Delta Toolbar installation seeking authorization in this program installation. This is very common. Standard today, in fact. What’s unique about this one, and why I chose it, as this one allows you to “see” what they are hiding, so it’s not so deceptive. Most of the time, the text and everything is COMPLETELY hidden, and you can’t see it until you either “uncheck” the default option, or “check” the advanced or custom option. I’ll say it again: “usually” it’s COMPLETELY hidden. I chose this picture, because in this install, you can see it. And I wanted one where you could see so I could show you.
Here’s another example: This one has the same Delta toolbar hidden under advanced installation, but even if you catch that one, don’t forget to click DECLINE “BEFORE” CLICKING NEXT!! so you don’t install the MIDI program also! (decline does not stop the installation, it prevents authorization for the malware program installation!)
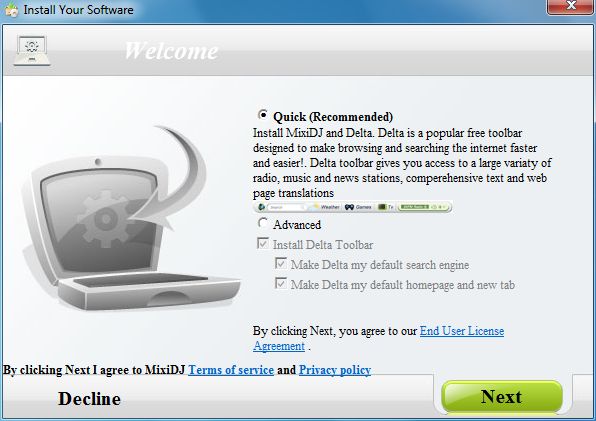
HiddenDeltaToolbar&aProgram
So here it is (the first example) once I unchecked the default, chose the advanced install, and UNCHECKED the additional nasty little Delta Toolbar. (all toolbars are nasty btw…never install any additional toolbars, NEVER!

The correct selections
So now hopefully you see how they hide those tricky things, and maybe next time, they won’t get you. 🙂
Remember, always choose advanced or custom program installations. You don’t have to be a technical genius to choose that option. That’s what the hackers want you to think.
![Are your website(s) rated as SECURE??]()
by E.I.T. Author | Dec 21, 2016 | Blog, Computers, internet stuff, Security, Web Development
If you have a website, you may have not even considered getting it rated as secure by the many website security rating systems that are out there, that display a security symbol next to your search results in Google & Bing. It looks something like this (this is Norton’s)  There are many of them, but the most popular ones are Norton’s Safe Web, WOT (web of trust), McAfee’s Site Advisor, Trend Micro’s “Trend Secure” …and so many others.
There are many of them, but the most popular ones are Norton’s Safe Web, WOT (web of trust), McAfee’s Site Advisor, Trend Micro’s “Trend Secure” …and so many others.
To get this, you would need to submit your site (and only the owner can do it)to Norton (or whichever rating service) for review, and then they give it that little green box stamp of approval next to the URL in the search results. For Norton’s Safeweb, You can submit it here: https://safeweb.norton.com/help/site_owners There are others also, if you want to deal with all of them, I don’t know, (I recommend doing as many as you can) but there is also Web of Trust (WOT), Webutation ( https://www.webutation.net/ ) McAfee Site Advisor (now called web advisor I think) (https://home.mcafee.com/root/landingpage.aspx?lpname=get-it-now&affid=0&cid=170789), AVG Threat Labs (https://www.avgthreatlabs.com/), Trend Micro’s TrendProtect, (https://test.trendsecure.com/portal2.1/en-US/free_security_tools/trendprotect.php?page=download) …and I’m sure there are others. I think Norton, Web of Trust, and Site/Web Advisor are the most commonly used ones.
Here’s a list of a few more if you’re interested: https://www.toptenreviews.com/software/articles/website-reputation-rating-tools/
Get your site that little green safe icon, because without it, you may just be losing traffic!
by E.I.T. Author | Dec 21, 2016 | Blog, Computers, internet stuff, Web Development
Do I know what they are? No, I don’t. I only that today is day 1, and today’s special is 50% off on all their hosting plans. So for a small site on their starter hosting plan, you can get it for $4 month, which works out to $48 for the first year, which is a very good price for hosting. I’ve been with them almost 10 years now…and I haven’t found a reason to leave. They have 24/7 support as well. Check it out here: GODADDY HOSTING PLANS ON SALE!
by E.I.T. Author | Dec 12, 2016 | Blog, Computers, hacking, internet stuff, Security, viruses
I was wondering when it would happen…that I would get a call from someone who had their files “ransomed”. What does that mean? Well the newest and greatest form of virus is ransomware…and it’s big business now. And they like to focus on businesses. They know that businesses can not afford to lose their client data…and they bank on that, and they quite often win.
Well, it happened today. And I felt bad for the guy.
What is ransomware? It’s a virus that installs one (or more) forms of ENCRYPTION on your computer, encrypts ALL your files so that they can not be opened without the decryption key, and it’s VERY effective. Some forms of ransomware can be decrypted, but there are some that can not. If your computer gets ransomed, you have only a couple of choices…
1. Pay the $500 or more to get the key and get your files back. If you want to do this, do it. Because once you start messing with trying to recover the files, you might lose the ability to decrypt…so think carefully about this. If you have no backup of your files, and you really need your files, and you can afford it, you should probably pay the money. It’s going to cost you maybe 1/3 to 1/2 that for an I.T. guy to remove the virus, and attempt to recover, and it may not even be possible. (though if you do, you should definitely get the machine cleaned after you get your files back!) You could possibly get a hold of the hacker, and try to negotiate a lower price I suppose, It’s worth a shot. I don’t know it’s successful or not.
2. You can remove the virus…to make sure no further files get encrypted, and start fresh…with the understanding that there is a 50% chance you will permanently lose your data. Every ransom attack is different. There are more than 1 ransom viruses, and some can be dealt with, and some can not.
3. You have a backup, and can restore it…GREAT! LET’S DO IT! Give me a call if you need help.
Some things to do once you know you have been hacked:
- Disconnect the internet! this can prevent cloud drive files from being synced to newly encrypted files, and being changed also if you have Google drive, or One Drive, or any other cloud account, and can prevent the virus from reaching other machines on the network.
- After you get the name of the ransomware package, write down the info, and SHUT DOWN THE MACHINE. Don’t use it. Don’t go on the network. Don’t install anything. Don’t do anything until you call a tech, or do some research on the internet on your particular ransom virus (from another computer)
- if you are going to try to remove it, download some help: Malwarebytes, Shadow Explorer, Norton Security (get a trial if you need to, they give you 30 days!)
- Often ransomware encrypts by way of making a copy, encrypting it, and deleting the original. Sometimes you can get originals back with deleted file recovery programs, like Recuva…which is an excellent program. System restore and Shadow Explorer will try to recover shadow copies created with system restore. If system restore doesn’t work, you can try to use ShadowExplorer.
If you haven’t been hacked yet, PROTECT YOURSELF!
- You should have a good security SUITE installed on every computer you own. If you don’t, shame on you! I can’t help you much if you don’t care enough to even try to protect yourself. I personally recommend Norton Security, it has the LEAST effect system resources (slowing down your machine) and it’s very good protection. And yes, you need the FULL SUITE of protection, firewall, virus scanner, real time protection…all of it, NOT JUST AN ANTIVIRUS PROGRAM. Malwarebytes is a good secondary protection. It will run alongside Norton just fine…and every time a new version releases, you get another 15 days of real time monitoring with it, (then it switches to manual scan mode, unless you purchase the pro version) …but 15 days of real time, 5 or 6 times a a year is fine for free, since you have another security suite, right? (yes) There is a 3rd program you can run alongside if you want, to protect specifically against ransomware, and it’s called CRYPTOPREVENT.
- Make sure SYSTEM RESTORE is TURNED ON and THAT YOU HAVE ENOUGH STORAGE SPACE FOR RESTORE POINTS! Depending what version of Windows you have, right click on either My Computer, or This PC (windows 8-10) and click on PROPERTIES. Then click on System Protection, select the drive you want to configure and then click CONFIGURE. You should turn on system restore for you operating system drive/partition, and any data partitions/drives you have. And you should also make sure that around 10% of the total drive space is allocated for restore points. (if you have system restore turned on, but have 0% space allotted to store restore points, it’s useless, as nothing will be written to the drive in way of a backup)
- BACKUP YOUR DATA. Cloud backup services are “ok” …for backing up files, but they won’t restore an entire drive image, operating system, and installed programs…it will only give you files. And it’s risky, because if it runs all the time, there is a chance those files also become corrupt when they sync with your machine. You should do regular full system drive imge backups with a backup program such as either Acronis True Image or Aeomi Backupper, or EaseUS Todo Backup . Do a FULL drive image backup at LEAST once a month (or incremental/differential if the software has that capability) If you do inc/diff backups, only do about 3 or so…but every 90 days at least, do a new FULL backup. Note, when doing backups, if you are using EXTERNALS USB HARD DRIVES, these will fail eventually. They have moving parts. They get hot. Especially if they run all the time, they will fail.. I myself use plain hard drives…if your desktop has storage for more hard drives, put a backup drive right in your machine. You can also use hard drives with a docking station, which is both cheaper, and more reliable than external drives. If possible, use flash storage: either flash drives (if you find one large enough) SSDs, or even SD cards can be used to store files, and they are typically more reliable. If you do use external hard drive, don’t leave it running all the time, and if you do need it to run all the time, get a new one every 18 months at least, sooner if you can afford it. Or, just store backups in more than one place. If you ever need one of your backups, you will be glad you have more than 1 to choose from. You really can’t be too anal about this stuff, trust me.
Anyway, that’s the skinny on ransomware. If you have questions, comment below, or contact Everything I.T. on the contact page (or just CHAT, we do that also) and we’ll give you hand!

by E.I.T. Author | Dec 9, 2016 | Blog, Computers, hacking, internet stuff, phishing, Security, viruses

You may have heard that more and more penetrations are coming by way of IoT devices. This may be new and confusing to you, and you may be wondering if this affects you, and how it could affect you.
IoT devices are devices that use, and connect to the internet, but because they are more simple in nature, haven’t been considered for security risks. One of the newest ones that has popped up is IP Cameras. An IP camera is a camera that transmits it’s data (images) in DIGITAL format instead of analog. How would you know if you had a digital IP camera? Well, analog cameras connect to recorders with coaxial cables, where digital IP cameras use a standard Ethernet (internet) cable. Here is an example of a digital IP camera: https://www.youtube.com/watch?v=79G4InvJX78 . If you have a newer security system in your home, or especially if you have a business with a full-fledged camera network security system, then this article on how Sony cameras are compromising networks would be a good, and highly recommended read for you. https://krebsonsecurity.com/2016/12/researchers-find-fresh-fodder-for-iot-attack-cannons/?platform=hootsuite My job is simply to educate you, and pass on new and important information, hoping to protect the public from the scoundrels and criminals who want to take advantage of your weaknesses.
Have a Happy Holiday season this 2016 Christmas and New Year. Blessings from Everything I.T.
by E.I.T. Author | Apr 28, 2016 | Blog, Computers, Email
I am FOREVER answering questions about email. And email explanations are usually lengthy. I get questions like “how to share an email address with my spouse” and set it up right…or, “How to set my email address up on my phone, tablet, AND computer so that it ‘does such and such’ or ‘doesn’t do such and such’ ” and how to set it up so that no emails are lost, folders are sync’ed, calendars are sync’ed, etc, etc.
Well, I found this excellent blog post that someone has already written for me. And since I can’t steal it (because that would not be ethical) and repost it here, and since it has really nice pictures to explain everything since so many people don’t want to take the time to read, cause that takes forever, I thought I would just send you there. Hope you don’t mind going to another site to read it:
How Do I Deal with One Email Account On Two Machines?






Recent Comments