
by E.I.T. Author | Feb 13, 2017 | Blog, Computers
Well, my last client motivated me. I have this new build that I want to dual-boot (actually I want to quad boot it) anyways, but since he got me started playing with Virtualbox, I decided to build a Mac Virtual Machine. Here’s a picture of it running…(click Read More button at bottom left) …you can run it full screen, but I wanted you to see that Mac & Windows are running at the same time, so I made the window smaller for purpose of the post.
It’s kind of cool this way, because you can share files and access programs in both operating systems (if you have enough processing power and memory) …if you dual/triple/quad boot, you can only run one operating system at a time. This way you have shared folders…

by E.I.T. Author | Feb 11, 2017 | Blog, Computers
So today, got to troubleshoot something different. Usually it’s either a Windows machine, or a Macintosh (OSX) or a smaller Mac (iOS) , or an Android. But rarely do I get to work on a Win-Mac. So today, a guy calls wanting to get his USB to work on His Windows install, inside of Virtualbox, inside of his Macbook. If you don’t know, Virtualbox is a Java program that lets you run any operating system inside of a virtual machine, inside of any other operating system. So today’s, his was Windows inside of OSX (Macintosh) …so it was quite fun. I love a challenge.
My next task is to run Mac (OSX) on a Windows machine. (also referred to as a ‘hackintosh’) …which is a slightly more difficult task. 🙂
Give me a call with your challenging task that’s giving you a headache, …and I’ll make it work for you!
by E.I.T. Author | Feb 1, 2017 | Blog, Computers, Security, viruses
Are you a person who sometimes gets viruses or malware on your computer, and you swear you didn’t install it, but you did, and you can’t figure out how or when it got slipped in there? Well I’m going to show you a common one that people miss.
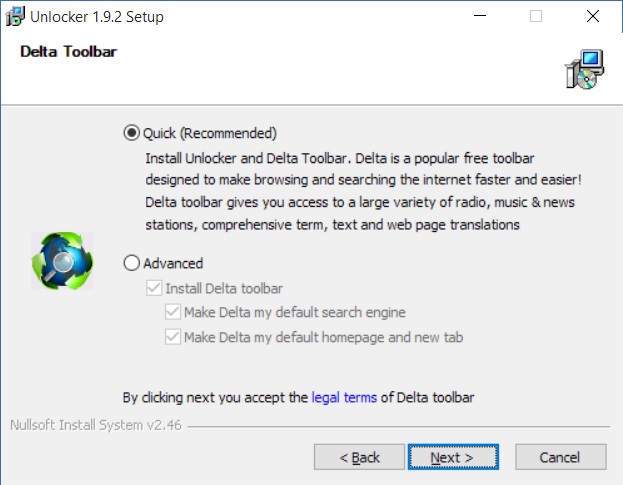
The problem now is, that hackers KNOW that most people select the DEFAULT, QUICK installation when they install things. So they hide them there. The solution? DON’T! Don’t select the default option when installing programs, EVER. Always choose the “ADVANCED” or “CUSTOM” installation when installing things. Always! I guarantee that 90-95% of the time, there is a toolbar, or some additional program installation needing your approval, set up in the default installation, and if you choose default, you “WILL” authorize it’s installation. I’m going to show you a picture, and as I run across other examples, I will come back and add more pictures to this post. But for now, I have two from today.

Hidden Toolbar in default program installation
Notice, that “if” I were to select the ADVANCED option, ONLY THEN can I UNCHECK the Delta Toolbar installation seeking authorization in this program installation. This is very common. Standard today, in fact. What’s unique about this one, and why I chose it, as this one allows you to “see” what they are hiding, so it’s not so deceptive. Most of the time, the text and everything is COMPLETELY hidden, and you can’t see it until you either “uncheck” the default option, or “check” the advanced or custom option. I’ll say it again: “usually” it’s COMPLETELY hidden. I chose this picture, because in this install, you can see it. And I wanted one where you could see so I could show you.
Here’s another example: This one has the same Delta toolbar hidden under advanced installation, but even if you catch that one, don’t forget to click DECLINE “BEFORE” CLICKING NEXT!! so you don’t install the MIDI program also! (decline does not stop the installation, it prevents authorization for the malware program installation!)
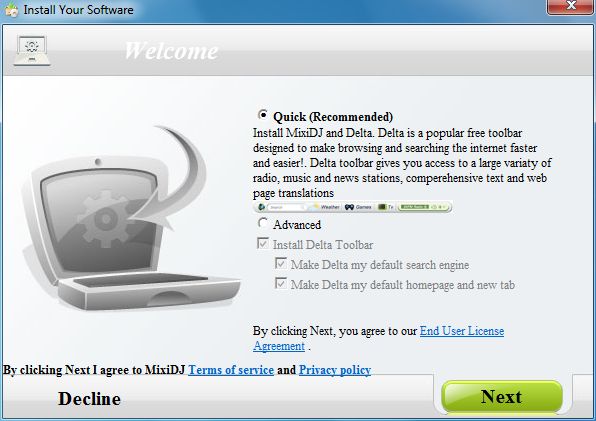
HiddenDeltaToolbar&aProgram
So here it is (the first example) once I unchecked the default, chose the advanced install, and UNCHECKED the additional nasty little Delta Toolbar. (all toolbars are nasty btw…never install any additional toolbars, NEVER!

The correct selections
So now hopefully you see how they hide those tricky things, and maybe next time, they won’t get you. 🙂
Remember, always choose advanced or custom program installations. You don’t have to be a technical genius to choose that option. That’s what the hackers want you to think.
by E.I.T. Author | Jan 12, 2017 | Blog
This post is to make you aware of a new Gmail email phishing attack that has fooled many experienced I.T. technicians and consultants. The only way to avoid it, is to be aware of how it works. Wordfence has done such a good post on this…so I won’t re-iterate all of their information. However, their post is quite long, and the information may just a little “too” deep for many to process through, so I will point out the highlights : To detect it, you have to FULLY read the address in the address bar, and it’s tricky. If you are reading Wordfence’s post, you need to go down about 1/3 down the page, to the picture of the address bar with the bright red arrow, and then some whitespace, and the script tag at the end of it….this is what you need to look for, and you have to select all the text to see as it will likely fall off the end and be hidden (which is intentional) There is also a paragraph titled “HOW TO PROTECT YOURSELF” READ THIS! That’s the important part! If you are able, I encourage you to read the entire thing. The post/information is HERE:
Also, there is some other great info in the post, and that is you can check any of your email addresses to see if they have been pawned anywhere… it’s a very reputable site, and THAT SITE IS HERE . If yours is RED, change your password!
by E.I.T. Author | Dec 27, 2016 | Blog
As you know, the web is getting crowded. And Google, being the primary search engine of choice, can’t possibly put everyone up in the front of the line. Google has a lot of policies to ensure that their clients find the best of the best, …first. Before all the crappy stuff. And that’s the way it should be. They have a lot (a really lot) of policies governing advertising…so if you use Adwords, you should really look. But this is not about advertising…
They have a new rule that governs sites that have forums, mailing lists, even simple contact forms…every site that takes personal information. And the rule is that those pages must be delivered via SSL (secure socket layer…encryption for you simple folk) In other words, they have to be able to be delivered with the https:// in the front, instead of https:// . And if they don’t comply, or can’t, then in Google’s search results, there will be a warning in red that the site is not secure. (damaging traffic, of course) If you want to read about it, The Post is Here
by E.I.T. Author | Dec 27, 2016 | Blog
I received a notice of this current excellent discount. It’s normally around $80 …but here, and now you can get it for $20 for the next 3 days…just click here: https://store.acronis.com/ It’s one of the best backup software utilities that exist… I love it. I’ve needed my backups more than once, and it’s great to make a backup when you are messing around with something that may break your machine (like trying to make a triple-boot on a GPT 3TB drive on a UEFI secure boot system! LOL)
Everything I.T. is not an affiliate of any organization, and we don’t make any money for bringing you the discounts we find. I just like to share what I find with my faithful followers. So stick around, and I’ll gladly share what I find with you…FREE.
Remember, backup, backup, and backup!






Recent Comments